I attended the World Economics Forum in Davos, Switzerland with a group of faculty from Carnegie Mellon. We were there to be the entertainment — we had earned our (otherwise very expensive) Davos badge by agreeing to present a panel session. I brought my camera (Fujifilm X-T1 with 18 mm lens) and took lots of photos. Here is a selection of photos and some thoughts on the whole Davos experience.
We arrived in Zurich and took the bus (provided by WEF) to Davos. It was about a 2.5 hour drive and the scenery got progressively snowier and more beautiful as we went along. We started meeting our fellow attendees on the bus, including McGill University principal, Suzanne Fortier, who was staying at our hotel, and later invited us to Montreal after return flights to the US were being cancelled.



We stayed at Club Hotel, a comfortable ski hotel (at high-end luxury hotel prices) at the far end of Davos from the Congress Center. This was the hotel that many of the academic speakers had been assigned to stay at. Across the street was a building with a big sign that said “Bernina.” As an owner of a Bernina sewing machine, I got very excited when I saw it, but it was just an apartment building… no sign of sewing machines. There was a shuttle stop on the corner across from the hotel, and shuttles came by frequently. However, at least once each day I did the 20-minute walk between the Congress Center and the hotel. Most of the daytime events were in and around the Congress Center, but some were in surrounding buildings, and most of the evening events were at hotels around the city.



The walk between the hotel and Congress Center took us past the storefronts and fancy hotels on the Promenade. Many companies (and even UC Berkeley) had rented out store fronts for the week. Some had been turned into Cafes where participants could stop in for a free lunch. Facebook had setup a house with a mini-museum that explained that it takes more energy to make a latte than it does to power one person’s Facebook usage for a year. There were police and security guards everywhere, but none seemed to be able to give directions. The best way to navigate was with Google maps, or looking for signposts along the way indicating the direction and walking distance between conference venues.





The weather was fairly pleasant, all considering. The temperature stayed around the high twenties with no wind. It snowed about every other day. My tall, waterproof leather boots (ECCO Babett 45 GTX) were perfect for the snowy weather, and I could wear them inside all day and was able to avoid carrying shoes around to change into. I was glad I brought a long down coat. With insulated tights, I was able to wear dresses comfortably all week without freezing when I went outside. Inside most buildings it was quite warm. We quickly got used to the process of arriving at a building (on foot or by shuttle); having our badges inspected by armed (but very friendly) guards; loading our bags, laptops, and coats onto the conveyor belt for screening; walking through the metal detector; collecting our bags; sometimes heading outside and then back into another building; scanning our badges; checking our coats (or holding on to them to save time); and finally getting to our destination.








On the first evening I attended the opening ceremony with awards presentations and a concert by Yo-yo Ma and a multi-cultural ensemble. Will.I.Am talked about education and Leonardo DiCaprio discussed global climate change While not exactly an expert in climate change, DiCaprio has apparently contributed a lot of money to the cause, and encouraged others to do likewise. I was surprised to see DiCaprio read his remarks, rarely looking up at the audience (the photo here is the only one I took where he is looking at the audience). Yo-Yo Ma’s performance was amazing, and worth sitting through the speeches to hear.



Following the opening session I found the shuttle to the InterContinental Hotel for the expert reception. Having just arrived, I was still wearing jeans and suddenly felt under dressed. I did not wear jeans again until I left for the airport to go home. Besides learning about Davos fashion, the expert reception was also a good introduction to eating at Davos, where sit down meals are few and far between for those of us not on the VIP lists. Coffee and alcoholic beverages were plentiful, but food required some foraging. We all got very good at spotting and making a bee line for waiters passing tasty, but small, snacks in the Congress Center or at whatever receptions we were attending.
I joined my colleagues, who were talking to John Green, author of The Fault in Our Stars, and his wife. When I arrived they were having an entertaining conversation about educational videos and it took a while for me to catch on and figure out who he was. John posted a brief video about his Davos experience after he got home.
I spent much of the next day practicing for and being nervous about my own talk. Three colleagues and I had been invited to Davos to do an “Ideas Lab” session, which uses the fun-to-watch but awful to prepare for Pecha Kucha format. We each had five minutes to give a talk with 15 slides (all images, no words), which advanced automatically every 20 seconds. We wrote out scripts weeks in advance and spent hours memorizing the scripts and checking the timing. I give talks and teach classes all the time, so public speaking comes pretty easily to me, but I don’t think I have memorized anything word-for-word since high school. Even the TEDx talk on passwords I gave a couple of years ago was easier to prepare. For my Davos, I made notecards, recorded myself reading my script and listened to myself over and over again, and practiced my talk repeatedly on the plane. The group of us did three rehearsals together before finally doing our session at Davos on Thursday, and again on Saturday. Our session was the Promise and Perils of the Connected Sensors. Two of my colleagues presented upbeat promise talks, one introduced security perils, and I finished out the panel with privacy perils. The talks were recorded and available here. (As you may notice in the video, I had two wireless mics attached to my sleeveless dress. The AV crew was used to putting mics on guys wearing suits, and wasn’t really sure how to attach the mics to me. They didn’t have surgical tape to tape the transmitter to my back so you’ll see one of the transmitters attached to the back of my dress with an antenna sticking up. The other one is in my boot with the wire running up my leg and under my dress.) There was also a scribe who made cool drawings while we talked.
The Ideas Lab session went very well, and we received a lot of positive feedback from attendees. Attendees at our session included a nobel laureate, a Microsoft executive, and Kofi Annan (yes, that’s him in the bottom right photo below). Connected sensors and the Internet of Things were topics that seemed to resonate with a lot of Davos people. Indeed, the toilets near the plenary hall in the Congress Center featured water sprays and dryers that could be controlled wirelessly through tablets mounted on the wall of each stall.







The CMU President, Subra Suresh, introduced our panel, and the dean of our School of Computer Science, Andrew Moore, participated in another Ideas Lab session that was moderated by NPR correspondent, Joe Palca. Some of our colleagues, including Justine Cassell, got to speak on the big stage in the plenary hall.




I attended a lot of sessions in the plenary hall of the Congress Center. This is where most of the heads of state spoke. In four days I saw the following government leaders speak: the Presidents of Switzerland, Cyprus and Mexico; Prime Ministers of Turkey, UK, Israel, and Canada; as well as John Kerry and Joe Biden (who was interesting, but went on much too long). UK Prime Minister David Cameron was the only head of state I saw speak standing in the middle of the stage with no notes, podium, or teleprompter. Benjamin Netanyahu had the funniest comments when he talked about Israel innovation and explained that Jewish Israeli cows make more milk per cow than any other cows and “every moo is computerized.”








Most thrilling, perhaps, was attending an interactive lunch with Canadian Prime Minister Justin Trudeau and several members of his cabinet. You could sign-up online for interactive lunches and dinners, but many of these events were full by the time academic attendees were allowed to sign up. After seeing that the lunch session I wanted to attend was full I noticed that the Canada lunch still had room so I signed myself up. Lunch was setup at banquet tables for a total of about 60 guests. A member of the cabinet was assigned to each table. When I came into the room I spotted a table that nobody was sitting at, with the name card Trudeau, so I sat down. Prime Minister Trudeau arrived late and when he came in he shook hands with Naheed Nenshi, the Mayor of Calgary, who was also seated at my table, and then took the microphone and began speaking. Trudeau gave his whole speech standing next to where I was sitting at the table. I snapped several good photos of him against the hotel’s butterfly wallpaper from where I was sitting 2 feet away. He finished his speech and left before I could get a selfie. (I did manage to get a selfie with Nenshi the next day when I ran into him at the Congress Center.) Nenshi was quite entertaining as he MCed the event, inviting the other cabinet members to make brief remarks and asking some pointed questions. I was quite impressed with Trudeau and the other cabinet members, who exhibited an energy and youthfulness that you usually don’t see in American politics. And they are incredibly diverse. Other than Trudeau, the cabinet members joked, they hadn’t brought with them any straight white guys.



My favorite session all week was a panel on “Progress towards Parity” with Melinda Gates, Sheryl Sandberg, and Justin Trudeau, along with SOHO CEO Zhang Xin and ManpowerGroup CEO Jonas Prising, When asked whether it was difficult to find enough qualified women to make his cabinet 50% women, Trudeau said the only thing difficult was choosing among all the great qualified candidates.

Other highlights included hearing US Secretary of Commerce Penny Pritzker talk about Safe Harbor on a panel with Microsoft President Brad Smith and others, watching Harvard Law Professor Jonathan Zittrain moderate a panel on the digital economy, and an interactive dinner for women in science. I took some pictures during Zittrain’s session and went up to talk with him afterwards. One of his panelists, YouTube CEO Susan Wojcicki, was eager to get a photo of herself on the WEF stage, so I told her I would send her the photos I had just taken. At the dinner I chatted with Joe Palca and his wife NIH Deputy Director Kathy Hudson, along with danah boyd.



There was a lot of discussion of refugees at Davos, and I attended an interesting simulation session called “A day in the life of a refugee.” As we entered the room, women were handed headscarves and we were told that for the next half an hour we were to obey the guards. A sound track of machine gun fire played, the lights went out, and we were eventually ushered into small, crowded tents. As we lined up for bread and water, guards took our jewelry and cell phones. It was an interesting simulation, but I think some of the power of the experience was lost as I was crawling around in tents with business executives wearing expensive suits. After the simulation concluded, we heard personal stories from people who had been refugees themselves or had worked at refugee camps. I found that to be the most compelling part of the session. As they returned our phones and jewelry. the session leader handed us postcards for feedback and asked us to list actions we could take to address the refugee problem. However, there had not been much discussion about what we could actually do.


I was interviewed for the Swiss public radio in a studio in the local public library, which had been turned into a media house.



There were not a lot of sessions related to my research interests. I attended an interactive session in which they talked about the growing number of people who were using ad blockers online. They broke us up into small groups, and I joined the group on “trust and user empowerment.” I was amused at this because I was giving talks on this topic as far back as 1997. When the moderator asked us what companies should do to build trust I suggested that companies should actually be trustworthy and actually empower users. This comment did not go over well with the corporate participates in my group. Later I attended a session on privacy that included a lively discussion by panelists who had somewhat limited expertise in privacy. A number of questions came up that the panelists didn’t have good answers for. During the audience Q&A I answered some of these questions and received a more positive reception. One of the panelists remarked that I should have been on the panel. I noted that most sessions seemed to follow an unwritten rule that there could be at most one woman or one academic on any panel, so this session was already at quota.

Between sessions we explored the Congress Center and the nearby Promenade. We discovered that the Microsoft Cafe served lunch. The lounges were good places for people watching, but it was sometimes difficult to find a seat. A few times I went into the plenary hall just so I could sit down and check my email. You never knew who you would run into in the Congress Center. If there were a lot of people with cameras, there was probably someone famous. Following the cameras led me to the Prime Minister of France, and IMF director Christine Lagarde.






The most unexpected celebrity encounter was meeting Yo-Yo Ma and his wife in the hallway of the Congress Center. I was introduced to them, shook hands, and mumbled something about being a computer science professor and having enjoyed his concert. Maybe I pointed to my password dress and said something about passwords. I only regret that I didn’t tell him I co-founded a company called Wombat Security and ask him about the time he was photographed on the floor with a wombat. Yo-Yo Ma was super friendly, and seemed to actually enjoy meeting all the people who were eager to shake his hand.

No Davos experience would be complete without Bono. I didn’t get to meet him, but I did see him on stage from the third row when he appeared briefly to celebrate the 10-year anniversary of the (RED) campaign.


Davos is not a great place for eating or sleeping. Before we arrived we had already received dozens of invitations to evening receptions at hotels around Davos. However, once we arrived we realized that our invitations were to only a small fraction of the parties that were taking place. We were able to talk our way into some of these parties, but many had fairly tight security. There were some interesting breakfast events every day but neither I nor any of my colleagues were able to get up early enough to attend them. CMU sponsored a small party at a local chocolate shop, but big companies and even countries sponsored enormous parties with open bars, food, swag, live music, and robots serving beer. Some hotels had so many parties going on that they posted electronic directories to help people find the parties they were looking for. Friday night I skipped most of the partying to attend the annual (and somewhat hard to get an invite to) Davos shabbat dinner. Sadly, the celebrities were no shows this year, but I did have an enjoyable evening.








The last evening in Davos was a formal soiree with music, a large buffet, and lots of swiss cheese. I wore a floor-length gown and 3-inch heels because I don’t have too many excuses to dress up, and how often do you get to wear a ball gown and pose with two St. Bernards? Unfortunately, we had to leave the ball early to rebook our cancelled flights due to East Coast US snow storm.




So how was Davos? The event is crazy and amazing, and not like anything I have ever been to before. The closest comparison I can make is South By Southwest. Only Davos is colder and had fewer artists, musicians, hipsters, and free tee shirts. And Southby is a festival and Davos is a place where heads of state go to talk to each other and everyone seems to have an agenda. I didn’t go with an agenda, other than to make it through my talk, take it all in, and help promote Carnegie Mellon. I met some interesting people, heard some interesting talks, saw lots of celebrities, and made a few contacts that may be useful for my research or my career.
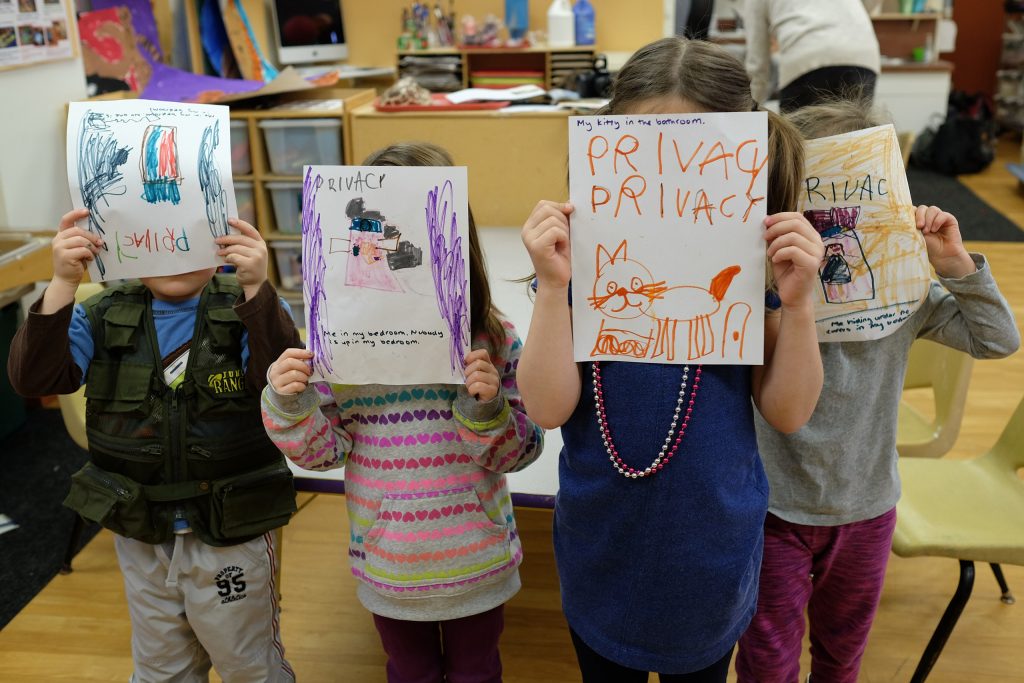










































































































































 I asked my students to extract the 1000 most popular passwords from the RockYou data set and provide a list to me with frequency counts. I then went through the list and sorted them into a number of thematic groups. I assigned a color to each group and entered the passwords with weights and colors into the
I asked my students to extract the 1000 most popular passwords from the RockYou data set and provide a list to me with frequency counts. I then went through the list and sorted them into a number of thematic groups. I assigned a color to each group and entered the passwords with weights and colors into the 





 Google’s approach is both clever and (with apologies to
Google’s approach is both clever and (with apologies to 





