The manner in which ballots are distributed, voted, collected, and counted is often as important as the system used for aggregating voter preferences. The system used can impact the overall voter turnout, the accessibility of the polls to all members of the voting population, the opportunity for fraud and vote tallying errors, the cost of conducting elections, the amount of thought voters put into their vote choices, and the electorate's confidence in the accuracy of the election results.
While a wide variety of voting systems and protocols exists, the basic procedure for conducting a democratic election is fairly standard. This procedure generally involves four tasks: registering voters, validating voter credentials, collecting voted ballots, and tallying the votes. This discussion will focus on the vote collection task, as it is most visible to the voters, and the protocols for performing the other tasks are often dependent on the way ballots are collected. Throughout this section, the term voting system will refer specifically to the ballot collection system.
Traditionally, governmental elections have been held at centralized precinct polling places, using hand- or computer-tallied paper ballots, mechanical voting machines, or direct-recording computer terminals. Large organization elections and recently some government elections are conducted via the postal mail. The possibility now exists for elections to be conducted via telephone, electronic mail, or the World Wide Web [35] as well. In this section some of the issues associated with each of these types of ballot collection systems are discussed.
There are many properties that ballot collection system designers might try to incorporate into their systems. The following properties are generally desirable, but not necessarily obtainable in all types of systems. These properties were assembled following several similar property lists found in the literature [11, 48, 80, 92, 95].
A system is accurate if (1) it is not possible for a vote to be altered, (2) it is not possible for a validated vote to be eliminated from the final tally, and (3) it is not possible for an invalid vote to be counted in the final tally.
In the most accurate systems the final vote tally must be perfect, either because no inaccuracies can be introduced or because all inaccuracies introduced can be detected and corrected. Partially accurate systems can detect but not necessarily correct inaccuracies. Accuracy can be measured in terms of the margin of error, the probability of error, or the number of points at which error can be introduced.
A system is convenient if it allows voters to cast their votes quickly, in one session, and with minimal equipment or special skills.
The convenience of a system is somewhat subjective, and depends not only on the system itself, but also on the voter population that will be using the system. For example, some populations might find it more convenient to vote at a centralized polling place using traditional voting methods while others might find it more convenient to vote from a personal computer in their homes or offices. For some populations it might be practical to locate centralized polling places at locations convenient to all voters; for other populations it will not be practical to do so.
A system is flexible if it allows a variety of ballot question formats including open-ended questions (this is important for write-in candidates and some survey questions).
A system is mobile if there are no restrictions (other than logistical ones) on the location from which a voter can cast a vote.
Systems that require votes to be cast at designated polling places are not mobile unless they have provisions for absentee ballots.
A system is private if (1) neither election authorities nor anyone else can link any ballot to the voter who cast it, and (2) no voter can prove that he or she voted in a particular way.
The second privacy factor is important for the prevention of vote buying and extortion. Voters can only sell their votes if they are able to prove to the buyer that they actually voted according to the buyer's wishes. Likewise, those who use extortion to force voters to vote in a particular way cannot succeed unless they can demand that voters prove that they voted as requested. Benaloh and Tuinstra explain:
There are reports that in some small Italian villages, the voting system employed allows voters to list their votes in any order. Political bosses are said to assign different permutations of their preferred candidates to each voter. If a particular permutation fails to appear when the votes are counted, a boss can assume that the voter to which that permutation was assigned did not vote ``properly'', and reprisals can be taken [11].
A system is verifiable if anyone can independently verify that all votes have been counted correctly.
A weaker definition of verifiability used by some authors [48, 92] allows that a system is verifiable if it allows voters to verify their own votes and correct any mistakes they might find without sacrificing privacy. Less verifiable systems might allow mistakes to be pointed out -- but not corrected -- or might allow verification of the process by party representatives but not by individual voters. Traditional voting systems generally only allow for minimal verification by party representatives.
A system is invulnerable, e.g. to ballot box stuffing, if (1) it permits only eligible voters to vote, and (2) it ensures that each eligible voter can vote only once.
In the United States, most national, state, and local voting takes place at centralized precinct voting places. The vote-collecting procedures vary greatly from precinct to precinct. Although some small precincts still use hand-tallied paper ballots, most precincts now use mechanical voting machines, direct-recording electronic voting machines, or machine-readable ballots.
Mechanical voting machines have a series of levers that voters pull to register their votes. Upon exit from the voting booth, the levers physically increment mechanical rotary counters. When the polls close, the backs of the voting machines are opened to reveal the vote tallies.
Machine-readable ballot systems, in use since 1964, require voters to mark their votes on a paper card with a pencil or marker, or remove divots from a perforated card with a stylus or mechanical hole puncher. The ballot cards are generally taken to a centralized computer center where they are scanned and tallied.
Direct-recording electronic voting machines require voters to use a keyboard, touch screen, or pointer to mark their ballot on a computer terminal. The votes are immediately added to a running tally.
Most traditional election systems are far from ideal. They tend to rely on a number of trusted parties who have the ability to conspire to change the outcome of the election or reveal the way particular voters voted. These systems generally work because most of the trusted parties are either trustworthy or have little trust in each other, and thus no conspiracy takes place. Although there has been much suspicion about security problems associated with computerized vote-tallying systems, there have been no proven cases of election fraud achieved through tampering with or manipulating such systems. All documented inaccuracies in computerized vote-tallying have been the result of problems with or misuse of the voting equipment or software. For example, a 1984 Carroll County, Maryland school board election was incorrectly tallied by a computerized tallying system after an election administrator accidentally installed the wrong utility program for reading ballot cards [39, 60, 93].
Experts disagree on whether it would be possible for a national election to be thrown by manipulating the computerized vote tallying system. Some see this as a real possibility, while others say it would be difficult for a national election to be thrown because of the large number of precincts (over 10,000) and the diversity of voting systems used. Most experts recommend that improvements be made to the vote tallying systems in widespread use and that selected precincts be tallied by hand to spot check the accuracy of these systems [39].
Regardless of the possibilities of tampering, electronic vote counting systems are attractive because they can count votes quickly and with minimal staff requirements, saving time and money. For example, Computerworld reported that the state of Oklahoma saved $1 million by introducing computerized vote counting in 1992 [56].
The punch-card system, the most widely used electronic vote tallying
system, has been heavily criticized for its susceptibility to
tampering and for its difficulty of use. Unlike direct-recording
systems and mechanical voting machines, the punch-card system does not
provide any automatic checks that the correct number of votes were
cast for each office on an individual's ballot. In addition, if
voters are not careful, paper bits called ``chad'' ![]() can remain attached to the back of the punch card and work their
way back into the holes that were punched. In 1987 it was found that
ballots cast in predominantly black wards in the city of St. Louis
were more than three times as likely to be improperly punched -- and
therefore not counted -- as those cast in predominantly white wards.
A federal judge subsequently ruled that the punch card system ``denies
blacks an equal opportunity with whites to participate in the
political process.'' The judge ordered the city to increase voter
education in black wards and count improperly marked ballots by
hand [39].
can remain attached to the back of the punch card and work their
way back into the holes that were punched. In 1987 it was found that
ballots cast in predominantly black wards in the city of St. Louis
were more than three times as likely to be improperly punched -- and
therefore not counted -- as those cast in predominantly white wards.
A federal judge subsequently ruled that the punch card system ``denies
blacks an equal opportunity with whites to participate in the
political process.'' The judge ordered the city to increase voter
education in black wards and count improperly marked ballots by
hand [39].
Traditionally, the accuracy of vote tallies has been verified by party observers. However, it is not possible for voters to verify that their individual ballots were counted correctly. When votes are tallied via computer or mechanical voting machine it often becomes more difficult to verify that votes are counted properly and that votes are not being systematically changed, added, or eliminated.
The use of absentee ballots gives national elections the mobility property, allowing voters to cast their votes from almost anywhere they want. However, absentee ballot systems tend to reduce privacy and increase the opportunity for ballots to be changed or lost.
Vote-by-mail balloting has long been used by large geographically distributed organizations. It has also been used by states for absentee balloting and for special elections and elections involving small precincts. Recently there has been increased interest in using vote-by-mail more widely in state elections. Vote-by-mail supporters claim this type of balloting usually results in increased rates of voter participation, less expensive elections, higher levels of election integrity, and increased accessibility for the elderly and disabled [4, 45, 81]. Opponents are critical of the levels of security and privacy associated with vote-by-mail balloting and sometimes suggest that the ease with which people can cast a ballot by mail makes them take the electoral process less seriously [23, 61].
Large professional, social, and special-interest organizations often hold their elections through simple vote-by-mail balloting systems. These systems are convenient for voters and vote talliers; however, they often sacrifice privacy because voters must write their names or identification codes on their ballots. Although these systems generally incorporate minimal security measures there are usually few problems because organizations that use them tend not to hold highly controversial elections. Some organizations hire a disinterested party (generally at considerable expense) to run their elections so as to prevent election fraud and obtain the staff support needed to process the ballots quickly.
Organizations using vote-by-mail systems need not sacrifice voter privacy or security. Voter privacy can be protected through the use of double-ballot envelopes and fraud can be prevented through careful tracking of ballots and auditing of the vote-counting process. For example, in April 1995, Fort Collins Colorado first used a PC-based ballot verification program called Voyager to track ballots in a vote-by-mail election. The city staff scanned bar codes on the ballot envelopes as they were received, enabling the system to track the return of ballots and expose voters' attempts to vote multiple times. Fort Collins Mayor Ann Azari reported that the vote-by-mail election resulted in ``increased voter turnout, compliance with ADA [Americans with Disabilities Act] requirements, elimination of the need to train and manage over 250 election judges and alternates -- and concerns about insurance coverage for 83 voting locations went away'' [4].
Indeed, with appropriate precautions, vote-by-mail can be suitable for even the most controversial elections. Probably the largest non-governmental organization to use vote-by-mail balloting to date is the Teamsters. In 1988 the Teamsters Union sent mail ballots to 1.5 million members. According to Teamsters election officers, the only problems encountered were a few attempts to vote multiple times or intimidate voters [73].
Many states use vote-by-mail balloting for some elections, especially in small precincts. For example, in the 1970s small precincts and water districts in California began using vote-by-mail balloting. Officials credited vote-by-mail with substantially increasing voter turnout while decreasing the costs of running these elections [73]. The state of Oregon began conducting some elections by mail in 1981. The first of these elections had an average voter participation rate of 78.1% and a cost of $.90 per vote cast, while the other elections held in the state that day had an average voter participation rate of 25.6% and cost $1.05 per vote cast. Subsequent vote-by-mail elections resulted in similar voter participation rates and cost savings [81]. Impressed by these results, law makers in other states began enacting laws permitting vote-by-mail balloting. By 1992 vote-by-mail elections were legal in 13 states [73].
In December 1995 Oregon held a vote-by-mail primary election to nominate candidates for a U.S. Senate vacancy, thus becoming the first state to conduct a mail-only primary election to nominate candidates for a federal office. Oregon held the general election for the vacant Senate position by mail in January 1996, and the state's Presidential preference primary by mail in March 1996. Citizen reaction to these vote-by-mail elections was generally favorable. A survey conducted by DRC Opinion Research in March 1995 found that 29.6% of the 604 respondents opposed using vote-by-mail balloting in the May primary and November general elections. Only 19% opposed using vote-by-mail balloting for these elections after they were informed that the state was likely to save $2 million for each election conducted by mail [85]. A telephone survey conducted by the Oregon Survey Research Laboratory following the January election found that 76.5% of the 1225 respondents ``favored vote-by-mail elections over polling place elections'' [97]. Another telephone survey of 1483 Oregon citizens found that respondents who indicated they had stamps in their home at the time they were interviewed were more likely to prefer vote-by-mail to polling place elections and more likely to describe vote-by-mail as convenient [100]. This suggests that some of the remaining opposition to vote-by-mail in Oregon is due to the fact that the state requires voters to pay their own return postage or hand deliver their ballots.
Besides the convenience and cost savings of vote-by-mail elections, some supporters also credit them with promoting ``cleaner campaigns, less demagoguery and maybe more intelligent discussion of the candidates and the issues'' [45] because voters have more time to examine their ballots and a longer time window (generally two to three weeks) in which to vote. Thus voters do not feel rushed to make their decisions and candidates gain little benefit from last minute attacks against their opponents.
Nonetheless, some people are skeptical still about the security of vote-by-mail balloting. The California and Kansas Supreme Courts have both ruled on cases involving vote-by-mail balloting. In both cases the courts refused to strike down laws allowing vote-by-mail balloting, despite the Kansas court acknowledging that ``vote by mail increases the potential for compromise of secrecy and opportunity for fraud'' [73]. Although media commentary on vote-by-mail has been mostly positive, some media organizations have expressed concerns. In December 1995, a Portland, Oregon radio station editorial criticized vote-by-mail for its lack of privacy and because it contributes to ``the loss of the voting ritual.'' The station argued:
If you're voting at home, a spouse may try to influence who you vote for and no one will report that. We've also been experiencing a wave of neglect and crime against the elderly by adult children. Influencing their vote would fit right in and there's nothing in the law that bans voting together with others at church or social clubs and there could be peer pressure to vote a certain way [61].
Bill Lunch, an Oregon State University political science professor agreed, ``If there are problems out there, we are not likely to hear about them because they involve husbands or wives or other family members trying to exercise undue influence on each other'' [23].
Oregon Secretary of State Phil Keisling dismisses concerns about vote-by-mail systems as pure speculation: ``As of now, we haven't has a single allegation of fraud or undue influence. A lot of concerns that have been raised have turned out to be the figments of some people's imagination'' [23]. Indeed, in a telephone survey conducted after the January 1996 vote-by-mail election, only four out of 1483 respondents indicated that they were not alone when they voted and that they would have voted differently if they had been alone [100].
Polls conducted after each Oregon vote-by-mail election held between 1981 and 1983 showed ``no undue influence to pressure a person to vote a certain way'' [81]. In fact, then Secretary of State Norma Paulus reported that vote-by-mail resulted in ``a significant increase in the integrity of elections'' due to the fact that voter signatures could be carefully verified, and ballots sent to voters who had moved without updating their registration were returned by the post office. In the first Oregon vote-by-mail election, 20.8% of the 25,913 ballots mailed were undeliverable and 127 ballots were rejected due to missing signatures or signature discrepancies. After investigation, six cases were referred to the attorney general for possible prosecution. In contrast, the challenge procedures used to detect vote fraud in traditional polling place elections are ``virtually ineffective'' [81].
...Democracy must be structurally modernized
must be mechanically implemented
to give it a one-individual-to-another
speed and spontaneity of reaction
commensurate with the speed and scope
of broadcast news
now world-wide in seconds.R. Buckminster Fuller, 1940 [49]
Futurist Buckminster Fuller was perhaps the first to suggest that voting be conducted electronically when he proposed ``electrified voting'' in his 1940 essay No More Secondhand God [49]. He wrote: ``This is a simple mechanical problem involving but fractional effort of that involved in distributing the daily mails to the nation.'' Although he gave no details as to how this was to be accomplished, his reference to telephone calls in the next paragraph of his essay suggests that he envisioned a telephone voting system.
Despite Fuller's optimism about the simplicity of building such a system, the task remained impractical until the advent of computers. In 1973 Vincent Campbell and Janet Santos demonstrated a ``televoting'' system by conducting a series of surveys for the San Jose Unified School District. Over 5,500 of the 180,000 people living in the district registered to participate in this National Science Foundation funded project. Voters were mailed information regarding each televote question along with voting instructions and secret televoter numbers. They were asked to call the televote computer and enter their televoter number and a three-digit code corresponding to the response most reflective of their opinion on the question at hand. A ``small eight-bit computer'' transferred the televotes onto magnetic tape. At the end of the week the data on the magnetic tapes was transferred via telephone to a commercial data processing firm so that the results could be tallied. The investigators estimated that for cities with populations of 50,000 to 500,000 people, a televote system would cost $25,000 to $30,000 to install and $.15 to $.50 per capita yearly to operate [25]. Although the demonstration proved successful, there was little interest in telephone voting until the 1990s.
In the Fall of 1992, Sandia National Labs conducted experimental vote-by-phone elections at four New Mexico high schools. Over 1500 students submitted mock votes via telephone. Afterwards, 95% of the students who tried the system said they would use such a system to vote in real elections if it were available. Mary Green, security specialist for high-risk applications at Sandia National Labs, told a Congressional committee that researchers had learned three things from this experiment:
(1) phone voting can be designed to be simple to use ...; (2) the volume of calls could overload your phone network so the period of phone voting would need to be extended; and (3) there are many ways to break into or sabotage such a system and only a few of these vulnerabilities have ready solutions [102].
Green outlined 10 objectives for secure phone voting and noted that the extent of the security risk varies with the type of election. She suggested that a secure phone voting system be ``designed such that, in order to break into it, an adversary would be forced to spend so much money and manpower that he could have `bought' all his voters or paid off elected officials for less money, less effort, and with less risk.'' She recommended that the U.S. pursue phone voting with extreme caution so as to prevent problems that might cause phone voting to ``be discredited for the next 30 years'' [102].
Other groups that tried phone voting in 1992 would have benefited from following Green's advice. A call-in poll conducted by CBS Television News and AT&T following George Bush's State of the Union Address on January 28, 1992 was the first test of large-scale telephone voting. This test proved problematic as only 314,786 of the 24.6 million calls to the vote-tallying computer got through. On June 6, 1992, the Nova Scotia Liberal Party held a province-wide election via telephone with the help of Maritime Telephone and Telegraph (MT&T). The election was held in conjunction with the party's conventions, with speeches televised for those who were not in attendance. The election was disrupted when MT&T's computer crashed and no backup systems were readily available. Adamson et al. suggest that the problems might have been avoided had MT&T or the Liberal Party researched the CBS experiment before proceeding [1].
Following the June 6 fiasco, MT&T compensated the Liberal Party financially for the failed election and the party agreed to a second attempt at vote-by-phone. For the second election, held on June 20, MT&T had a bank of operators standing by to record the vote manually should the computer system fail. They had also guaranteed their system by posting a $350,000 performance bond. This time everything went smoothly and by the end of the day almost 14,000 votes were collected and tallied in two rounds of balloting [1]. The voter participation rate was four times greater than it had been for the party's previous election, which had been conducted via traditional means at a party convention [58].
On September 11, 1993, the Liberal Party of British Columbia held a vote-by-phone election. This election also used MT&T's televoting system and proceeded without any technical difficulties. Surveys conducted after the Nova Scotia and British Columbia elections indicate that a large majority of voters prefer the televoting system to paper ballots, delegate conventions, and other voting methods. A majority of those surveyed believe that televoting is more convenient, cost effective, and easier to use than paper balloting. The majority of registered voters surveyed said televoting was more private and secure than paper balloting, while the majority of those surveyed who were not registered to vote felt that paper balloting was more secure and private. Critics expressed some concern that candidates might buy voters' secret access numbers so that they could cast large blocks of ballots. However, only 9% of the voters surveyed indicated that someone else had voted on their behalf, and (although it was not requested) some provided explanations that ``anyone would agree were innocent'' [15].
Following the successful Liberal Party televotes, MT&T created a wholly-owned subsidiary, MT&T Technologies, to develop and market telephone voting and surveying services. The company established a high-security ``Teledemocracy Centre'' in Halifax, Nova Scotia, which houses all of the computer equipment necessary to run a vote-by-phone election and provides accommodations for personnel who must be sequestered for the duration of an election. The Teledemocracy hardware currently includes a series of IBM RISC System/6000 processors and 480 telephone lines [71].
Despite the success of telephone voting in Canada, this technology has been relegated to media polls and pay-for-vote publicity stunts in the United States. William Kimberling, a Federal Elections Commission official, told the Wall Street Journal in 1992 that the public was not ready for telephone voting. ``The futuristic stuff is good for people who watch Star Trek regularly, but not my mother,'' he stated [58]. Efforts to adopt telephone voting for municipal elections have so far been unsuccessful. In 1993, a group of Colorado citizens placed an initiative mandating that vote-by-phone be used for citizens' initiatives and referenda on the Boulder ballot. The initiative received a 41% ``yes'' vote, but did not pass. Supporters attributed the failure to misconceptions about the security associated with telephone voting [83].
Security has long been an important consideration for electronic voting systems implemented over computer networks rather than telephone networks. Much work has been done to develop cryptographic protocols that are both secure and private. In addition, these protocols often possess additional properties, such as complete verifiability, which are not generally obtainable in traditional voting systems.
David Chaum published the first cryptographic voting protocol in a
1981 paper on anonymous electronic mail and digital
pseudonyms [28]. This protocol uses public-key
cryptography![]() and relies on
rosters of digital pseudonyms to conceal the identity of voters.
However, the protocol does not guarantee that the identity of voters
cannot be traced. Chaum later proposed a protocol that
unconditionally conceals the identity of voters [30].
However, elections conducted with this protocol can be disrupted by a
single voter. Although Chaum's protocol can detect such disruptions,
it cannot recover from them without restarting the entire
election [57].
and relies on
rosters of digital pseudonyms to conceal the identity of voters.
However, the protocol does not guarantee that the identity of voters
cannot be traced. Chaum later proposed a protocol that
unconditionally conceals the identity of voters [30].
However, elections conducted with this protocol can be disrupted by a
single voter. Although Chaum's protocol can detect such disruptions,
it cannot recover from them without restarting the entire
election [57].
In 1985, Cohen (a.k.a. Benaloh) and Fischer published a description of a secure election scheme in which it is very difficult for dishonest voters to disrupt the election [32]. However, the scheme does not protect the privacy of individuals from the election authority. Cohen later presented extensions to this scheme which distribute the power of government and offer more privacy protection [31]. Benaloh claims this scheme is ``reasonably practical'' and cites political problems as a greater hindrance to implementation than technical problems. However, he also acknowledges that knowledge of college-level mathematics is required for voters to verify election results independently [12]. In addition, because of the scheme's large communication complexity, casting a vote may take an unacceptably long time [91].
In 1994, Benaloh and Tuinstra proposed a set of verifiable secret-ballot election protocols that do not allow voters to prove the contents of their votes [11]. Unlike the other cryptographic protocols discussed here, these protocols require voters to vote inside a voting booth. The authors maintain that the simplest of their protocols does not require computations on the part of the voter that are outside ``the range of normal human ability.'' However, the more complex protocols that have fewer requirements for trusting election authorities would require the voter to bring a personal computing device into the voting booth. Even their most sophisticated protocol does not guarantee that voters cannot be coerced, unless one or more election authorities are trustworthy. Although not a practical solution for Internet voting, the receipt-free nature of this system is significant because it prevents voters from participating in vote buying schemes.
A number of other cryptographic voting schemes have been proposed that require interactions between voters. These schemes, including [37], may be useful in a boardroom setting, but are not suitable for most large-scale elections.
The more practical cryptographic schemes do not require any
interaction between voters or use of specialized equipment. However,
none of these schemes prevent vote buying. One of the more simplistic
of these schemes requires two electronic election authorities: a
validator and a tallier. In this scheme, shown in
Figure ![]() , voters encrypt their ballots with the
tallier's public key, sign them, and forward them to the validator.
The validator strips off the voters' signatures, checks to make sure
the ballots were submitted by registered voters who had not yet voted,
and forwards the ballots to the tallier. The tallier decrypts the
ballots and records the votes. This scheme prevents non-registered
voters from voting and registered voters from voting multiple times.
However, it only protects voters' privacy if the tallier and validator
do not collude. In addition, it does not provide a mechanism for
voters to verify that their votes were counted correctly.
, voters encrypt their ballots with the
tallier's public key, sign them, and forward them to the validator.
The validator strips off the voters' signatures, checks to make sure
the ballots were submitted by registered voters who had not yet voted,
and forwards the ballots to the tallier. The tallier decrypts the
ballots and records the votes. This scheme prevents non-registered
voters from voting and registered voters from voting multiple times.
However, it only protects voters' privacy if the tallier and validator
do not collude. In addition, it does not provide a mechanism for
voters to verify that their votes were counted correctly.
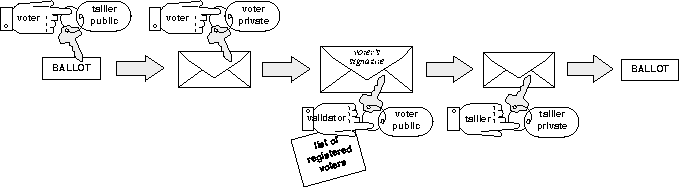
Figure: A simplistic voting protocol
In the Two Agency Protocol developed by Nurmi, Salomaa, and Santean [80], the responsibilities of validating registered voters and computing and publishing the results of the election are divided between two agencies, as in the simplistic scheme. In this protocol the validator distributes a secret identification tag to each voter just prior to the election. The validator then sends the tallier a list of all identification tags, with no record of the corresponding voters. Each voter sends the tallier his or her identification tag and an encrypted file containing a copy of the tag and the voted ballot. At this point the tallier can make sure the identification tag is valid, but the program has no way of examining the contents of the ballot. The tallier publishes the encrypted file, and the voter responds by sending the tallier the key necessary to decrypt it. When the election is over, the tallier publishes a list of all voted ballots and the corresponding encrypted files. At this point the voters can confirm that their votes were counted properly. Any voter who finds an error can protest by submitting the encrypted file and decryption key again. Because the encrypted file was published earlier, the tallier cannot deny having received it.
The Two Agency Protocol is verifiable by individual voters (unlike the simple protocol discussed earlier), however, it still has several problems. Most importantly, it does not protect voters' privacy if the tallier and validator collude. Thus, the authors state that if the two agencies are going to work together, there might as well be just one agency [92].
The One Agency Protocol is identical to the Two Agency Protocol, except for the tag distribution procedure. In the One Agency Protocol, tags are distributed by the tallier (there is no validator) using an ANDOS (all-or-nothing disclosure of secrets) protocol for secret selling of secrets. This solves the collusion problem; however, the ANDOS protocol is quite computationally complex and does not scale well. Another problem with both the One and Two Agency Protocols is that the tallier may cast votes for all voters who have been assigned a tag but do not exercise their right to vote [92, 80].
When Chaum first introduced the concept of blind
signatures![]() in 1981 [28], he suggested that blind signatures could be
used for secret-ballot elections. Ten years later, Fujioka, Okamoto,
and Ohta developed a practical voting scheme that uses blind
signatures to solve the collusion problem inherent in protocols like
the Two Agency Protocol without significantly increasing the overall
complexity of the protocol [48]. (A number of other, less
satisfactory blind signature protocols have also been proposed. Sako,
for example, proposed a protocol that is simpler but does not
completely prevent election administrators from linking ballots with
the voters who cast them [90].) The Sensus
protocol [35] is based closely on the Fujioka, Okamoto, and
Ohta scheme. The main difference between these schemes emerges after
the voter has submitted the encrypted ballot to the tallier. In the
Sensus protocol, the tallier responds by sending a receipt to the
voter. The voter may submit the decryption key immediately after
receiving this receipt, completing the entire voting process in one
session (verification must still wait until the election is over). In
the Fujioka, Okamoto, and Ohta, protocol the tallier responds by
placing the encrypted ballot on a list that is published after all
voters vote. Thus, a voter cannot submit his or her decryption key
until after the voting phase of the election is over. As a result,
votes cannot be cast in a single session.
in 1981 [28], he suggested that blind signatures could be
used for secret-ballot elections. Ten years later, Fujioka, Okamoto,
and Ohta developed a practical voting scheme that uses blind
signatures to solve the collusion problem inherent in protocols like
the Two Agency Protocol without significantly increasing the overall
complexity of the protocol [48]. (A number of other, less
satisfactory blind signature protocols have also been proposed. Sako,
for example, proposed a protocol that is simpler but does not
completely prevent election administrators from linking ballots with
the voters who cast them [90].) The Sensus
protocol [35] is based closely on the Fujioka, Okamoto, and
Ohta scheme. The main difference between these schemes emerges after
the voter has submitted the encrypted ballot to the tallier. In the
Sensus protocol, the tallier responds by sending a receipt to the
voter. The voter may submit the decryption key immediately after
receiving this receipt, completing the entire voting process in one
session (verification must still wait until the election is over). In
the Fujioka, Okamoto, and Ohta, protocol the tallier responds by
placing the encrypted ballot on a list that is published after all
voters vote. Thus, a voter cannot submit his or her decryption key
until after the voting phase of the election is over. As a result,
votes cannot be cast in a single session.
The Sensus protocol satisfies most of the desirable properties of voting systems well; however, it fails to correct one of the problems inherent in the One and Two Agency protocols: the election administrators (in this case the validator) can cast votes for abstaining voters. These invalid votes can be detected by the abstaining voters themselves or by an auditor who checks the signatures on all the validation requests submitted. However, there is no way to identify the invalid ballots and remove them from the tally. If voters who wish to abstain submit blank ballots, then this problem can be avoided. Another problem with the Sensus protocol is that it requires voters to participate in a complex set of transactions in order to cast a vote. However, the Sensus system employs a pollster module that acts as an agent on a voter's behalf, allowing these transactions to be performed with ease. Tests conducted with the Sensus prototype indicate the entire voting process can be completed within a few minutes. While the literature contains many descriptions of cryptographic voting systems, the Sensus system is one of the few cryptographic electronic voting systems to have been built [35]. Another variation of the Fujioka, Okamoto, and Ohta protocol was implemented by Davenport, Newberger, and Woodard [36] and used to conduct student government elections at Princeton University in 1995 and 1996.
Electronic voting has become increasingly popular for use in university elections due to the easy accessibility of computers on college campuses and the relatively low expense of conducting such elections. In 1994, the Association of Graduate Engineering Students at Washington University conducted a referendum election using a simple email voting system. The system resulted in a much higher rate of participation than the organization had previously experienced using traditional voting methods. Electronic voting has also been used successfully at other universities including Dartmouth, Bowling Green, MIT, and Miami of Ohio [5].
Electronic voting has proven controversial on some campuses. At the University of Maryland-Baltimore County, a proposal to conduct student government elections electronically resulted in a heated debate and eventually the withdrawal of the plan. While some members of the campus election board attributed the decision not to proceed with electronic voting to concerns about the security of the system, others maintained that it was politically motivated. The 1995-96 student body president, Lamont King, had been elected with 444 votes in an election in which voter participation was less than 10%. Some students said King feared that the greater voter participation that was likely to accompany an electronic election would require him to put more effort into campaigning outside his own circle of friends and make it more difficult for him to get re-elected. Although the election was eventually conducted via traditional means, King was disqualified after arriving late to a mandatory candidates' meeting, and a write-in slate composed of self-described ``computer geeks'' won the election [5].
Electronic voting has also become popular on the World Wide Web. Informal Web surveys are easy to implement when security and privacy concerns are ignored (as they usually are). Alexia Parks' Votelink is perhaps the best example of such Web-based voting. The Votelink site invites visitors to vote on a variety of local, national, and international issues. Site maintainers claim that their results are often similar to the results obtained using traditional survey methods. In addition, Votelink has begun working with officials in San Mateo County, California to conduct secure, online polls on issues of local importance [105].
In August 1996, the Reform Party became the first US political party to use Internet and telephone voting to select a Presidential candidate. Voters could also vote in person at the party convention or submit their ballots via postal mail. Regardless of the voting method used, voters' names were affixed to their ballots, eliminating any possibility of a secret ballot. According to a party spokesperson, the party mailed 1.13 million ballots to its members. Voters returned 43,202 paper ballots (via postal mail or at the party convention). Only 3963 voters phoned in their votes and 2101 voters voted via the Internet. The small percentage of voters voting via telephone or computer might be attributable to the fact that the information mailed to voters did not include the toll free phone numbers (the numbers were announced at the convention and in media reports) and included minimal instructions for Internet voting.
Supporters of direct democracy promote electronic voting (via telephone or computer) as a practical solution to the technical problems of polling the entire electorate regularly [83]. Proponents of such schemes include members of the Democratech Party of British Columbia, who advocate governmental decision-making through electronic referenda [22].
When properly designed, electronic voting systems should be suitable for a variety of polling applications, including large-scale elections. Although electronic governmental elections may be months or years in the future, political parties, and professional and social organizations have already started to conduct surveys and elections electronically. While most of these elections currently ignore privacy concerns, advances in email and Web browser software that can easily interface with cryptography software should pave the way for secure and private electronic elections in the near future.